APTs, iPhone Fingerprint Readers, and Complex Passwords: Why you should fire your IT Security Team
Whoa, kind of an aggressive title, I know. It's a bit of hyperbole, but many IT security teams are failing their organizations badly. How?

The Problem
The way the most of the IT industry thinks about security is idiotic, and has been shaped by vendors to help sell stuff. It’s always painted as some infosec cold war- The white hat IT security folks at your organization versus some Bond villian-eque hacker in some bunker somewhere. It sells to the business’ fear of the unknown and the IT team’s superhero complex.
Who are the real Threats?
In actuality, IT security is actually no different than any other risk vs. cost tradeoff. It follows the law of diminishing returns- and the curve bends quickly and then is a slow taper. Not counting insiders (who are actually the #1 liability to every organization), there are really three classes of threats-
- Sophisticated and well funded(nation state or equivalent)
- Sophisticated and not well funded (experienced/thorough individual)
- Unsophisticated ( novice/‘script kiddie’)
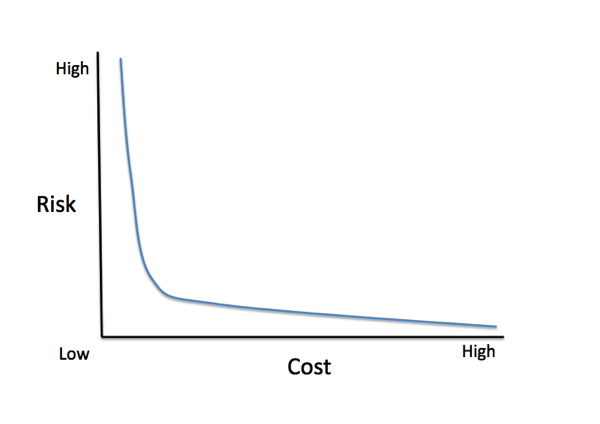
Stopping the first group requires a huge investment and a relentless culture to keep out, and even then they may still get in. Your best defense against that group (call them APTs if you must) is hopefully you don’t have anything they actually want.
Stopping the latter groups just requires following good basic (actually valid and usually free!) security measures like password lengths (passphrases), keeping up with patches, keeping unneeded ports/services disabled, training users on good security practices especially social engineering. Anything you do on top of that for most organizations is 1) not worth the investment for the minuscule risk reduction 2) is even more costly as it impacts actual productivity. It’s the security equivalent of talking IT staffs into wearing clean room suits every time their go in their datacenter to reduce the risk of device failure due to static discharge.
That’s not even counting the stuff like complex password policies and expirations that at best don’t improve your security and at worst make it weaker (Relevant XKCD).
Never mind that most of these measures don’t deal with malicious insiders, nor can they. As the NSA can probably tell you, once you give someone access there is little you can do to stop them from accessing it. Your defense there is other employees, hiring, culture; not software or hardware.
Enter the iPhone

The recent technology news surrounding the iPhone 5S's fingerprint reader is a great example. Once it was announced, the predicable responses came; talk of how it could be defeated by hackers with special equipment, or how it "wasn't secure enough" and should require a passcode as well as the fingerprint.
As Chris Hoff (@Beaker) so eloquently pointed out, it's not a security feature, its a convenience feature:
- It provides better security than no lock at all (many users don't use passcode locks)
- What's being protected by it on the device (photos, texts, emails) aren't generally sensitive enough for someone to go through all the trouble of bypassing the scanner
- If someone is willing to go through that level of effort, they would find other ways to access your data anyway. (Revelvant XKCD again)
Conclusion
The inability of the average IT department to think in different protections for different levels of risks, and to do the risk vs cost (both money and lost productivity) analysis leaves businesses frustrated (@MikeFoley's favorite "IT Security puts the 'no' in innovation" quip) and at greater risk. With any security change that brings *any* additional burden to the users or cost to the organization, you have to clarify what the risk reduction is and if it's worth it.